If you saw me right now, you would probably ask if I had just seen a ghost. After reading several articles about a new extremely dangerous and destructive form of ransomware, I feel like I’m facing Freddy Krueger!
This is the kind of attack that keeps IT professionals up at night.
Most viruses, rootkits, and malware are annoyances and can be removed by tools that are readily available on the internet. While some can be removed pretty quickly with killer apps like MalwareBytes, others may be more tenacious and require a recovery of your files and reinstallation of your operating system, a process that will take hours or days and cost a pretty penny. However, at the end of the day, all of your files can be safely restored either from your hard drive or a recent backup (you ARE backing up right?) ![]()
This one is different. It’s called CryptoLocker and it will ruin your day. Here’s what it does:
CryptoLocker is a ransomware program that was released around the beginning of September 2013. This infection will encrypt certain files using a mixture of RSA & AES encryption. When it has finished encrypting your files, it will display a CryptoLocker payment program that prompts you to send a ransom of either $100 or $300 in order to decrypt the files. This screen will also display a timer stating that you have 96 hours, or 4 days, to pay the ransom or it will delete your encryption key and you will not have any way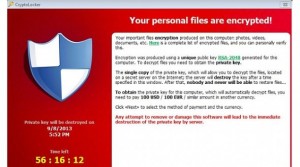 to decrypt your files. This ransom must be paid using MoneyPak vouchers or Bitcoins. Once you send the payment and it is verified, the program will decrypt the files that it encrypted. (thanks to Lawrence Abrams on BleepingComputer.com for this summary)
to decrypt your files. This ransom must be paid using MoneyPak vouchers or Bitcoins. Once you send the payment and it is verified, the program will decrypt the files that it encrypted. (thanks to Lawrence Abrams on BleepingComputer.com for this summary)
How do you become infected with CrptoLocker:
Currently, the infection is spread through emails pretending to be customer support notices from Fedex, UPS, DHL, etc. and the attachment is typically named Form_102213.pdf or Form_102213.pdf.exe (or some variant of these), but might also be disguised as a ZIP or other file type.
What if you get infected:
The first thing to do is disconnect your computer from the internet – this will prevent encryption of additional files. If you’re working wirelessly, disable wireless on your PC. If connected via Ethernet cable, pull the plug. Next call your IT pro and start deciding how important your encrypted files are to you. Also, figure out where your most recent backup is and how recently it was completed. Most cloud-based backup services provide file versioning for a period of time. For example, Carbonite saves previous versions of files for 3 months which could be your saving grace.
Removal of the malware seems to be straightforward according to the articles. However, without the decryption keys it is absolutely impossible to decrypt your files. Thus, if you cannot recover the files from a recent backup and need them restored, your only option is to act quickly and send the ransom money. There is currently no tool available (or IT Pro) that can decrypt your files.
How to protect yourself:
1. Be vigilant about opening email attachments – never open an attachment originating from unknown/unexpected sources (i.e. if you’re not traveling anywhere, don’t open a travel itinerary from Delta!). Also, be careful when opening unusual attachments from trusted sources as their email may have been hacked.
2. Be very careful about free software you download from the internet.
3. Backup to an external hard drive ($85 for 1TB) and disconnect it from your computer or use an online service that provides versioning.
4. Keep all programs updated and Windows Updates applied.
5. Make sure you’re running System Restore on your PC. This can help recover previous versions of files that have been encrypted.
6. Apply the Software Restriction Policies outlined in this article using Local Security Policy or Group Policy (domain computers) to disable the malware’s ability to execute on your system. This is fairly advanced, so please let me know if you want assistance applying these policies to your PC. Also, keep in mind that these policies will block the malware in its current form. If the hackers modify the code to install from another location on your computer, these policies will not protect you.
The above tips can help mitigate the risk but the best tip is not to open suspicious files. Tip #6 is the best available protection in the event that you accidentally open a file and obtain the infection in its current form.
One last comment on updates: Don’t forget that Microsoft is ending support for Windows XP in April, 2014. Expect threats like this on XP machines to heat up following the support sunset.
If you want to geek out on more technical details about the threat, take a look at these articles posted on BleepingComputer.com, MalwareBytes and Microsoft.
Stay safe out there!