Somebody’s Watching Me
If you listen to the 80s station on Sirius/XM, you’re undoubtedly getting tired of Rockwell’s sole hit, Somebody’s Watching Me. Since Al Gore was still working out the kinks of the internet, I imagine that Rockwell was not singing about online security. Instead, he was probably more worried about paying off Michael Jackson for backup vocals on the song’s chorus, since there were no other hits on his debut album. 
On a completely different note, I recently attended a very informative presentation on social media in which the speaker discussed the risks and rewards of social media. Since the audience consisted of parents of middle- and high school students, he focused on the risks facing children and teens and how to keep them safe online.
I walked away comforted that everyone in the room knew a little more about online risks and were better prepared to watch over their kids as they navigated the world of social media. However, I couldn’t help wondering who might be watching over the parents and their technology. In other words, are folks taking appropriate precautions to protect their computers and networks? So, I compiled a quick and dirty list of a few things you can do to stay safe on the world wide web. Rather than going into detail on how to configure all of these options, I have tried to keep it brief. Feel free to post follow-up questions if you need further guidance. Look for follow-up articles in the future that address some of these options.
Secure your wireless network:
Without a secure wireless network, anyone within shouting distance of your house can access the internet using your connection to download whatever they want on *your* network IP address. Further, with the right tools (which are widely available on the internet) they can “listen” in on your connection, and may even be able to access files on your computer(s).
Securing your wireless network is much easier than it used to be. Where it once required careful review of the Owners Manual, newer wireless routers can have you surfing securely with the push of a button. Always select the highest security offered by your router. WEP can be quickly cracked by a determined intruder, so use WPA or WPA2 if your wireless router supports it.
Avoid Using Public Computers to Login to Your Secure Accounts:
Sure, we’ve all been in a pinch before and logged into email on a public computer. However, that was before I knew what I know now. There’s absolutely no way to tell if a public computer is infected with malware, has keyloggers installed or other methods which can steal your credentials. Malware can grab user names & passwords and beam your information to the mother ship. Likewise, keyloggers can track every keystroke you make and report back to a hacker. Thus, browse online news and weather on the hotel’s business center computer. Save online shopping, banking, and even email until you get back to a safe connection.
Use Antivirus Software and Keep it Updated
This one is a no-brainer. If you have not been affected by viruses/malware in the past, you will eventually. Fortunately, you don’t have to pull out your wallet to stay safe, as discussed in my post on free antivirus options. Use one of the packages that I recommend or choose one you like by reviewing AV-Test’s ratings.
Online Banking, Shopping and Secure Sites:
Ever notice how your address bar turns green, shows a padlock and/or the address changes from http:// to https:// when you login to your bank or shopping site? This assures you that your connection is encrypted, that the identity of the website has been verified by a third party and that it’s safe to send sensitive information such as your username, password and credit card information over the internet. In fact, if you click on the green portion in the address bar or the padlock, you will see that the website’s identity has been verified by VeriSign, Thawte or another certificate authority (“CA”). So while it seems like you’re just connecting to a remote website, there’s actually a lot of stuff going on in the background to verify to your browser that the website is authentic, that your transmissions across the internet are encrypted and that it’s safe to do business.
But what if you attempt to log into a shopping or banking site that should be secure and it is not, in fact, safe? If you don’t get the https://, the green bar/padlock or you receive warnings that the site’s certificate has problems, check the address that you typed. If it’s correct, get out and try again later. It may be a temporary glitch with the site’s certificate or the CA. It’s not worth compromising your security and identity to buy ABBA’s Greatest Hits on an unsafe connection.
Be Careful Using Public Wireless Networks
Free wireless offered by coffee shops and other retailers helps offset Starbucks’ exorbitant coffee prices, but be cautious with your browsing on public networks. This may seem a bit paranoid, but I never do online banking or shopping on a public wireless network, even from my own laptop. Yeah, I know that the connection to the bank or Amazon is encrypted, but I have no control over the coffee shop’s wireless security so I would rather be safe than sorry.
The kid in the corner booth with the AlienWare laptop may be listening in on your connection using a packet sniffer, which is freely available on the internet. Further, if your firewall is turned off, you have shared folders turned on, or your operating system has not been patched, a determined hacker can easily access the files on your PC.
Windows 7 and Vista both make it easier to stay safe on public networks than XP. When you connect to a new wireless network, the Set Network Location provides 3 choices of network location types: Home, Work and Public. Always choose Public when out and about. This sets your firewall at its highest security settings, turns off Network Discovery and file sharing options, providing higher security when on a public network. 
As a follow-up, make sure your mail connection is encrypted (see https:// discussion above). Many webmail systems are not encrypted by default, but offer this option. If your email provider offers secure browser connections (thanks, Gmail!) always turn it on. If you trust the network you’re using, it may be safe to disable.
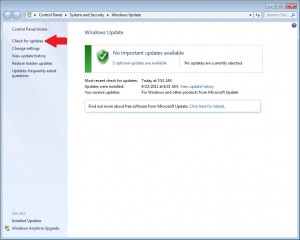
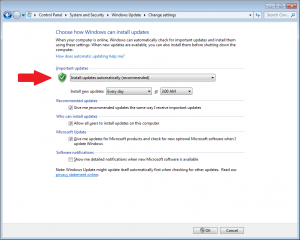
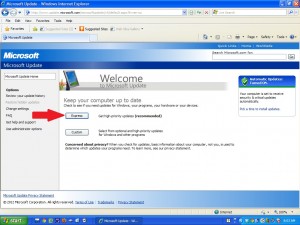
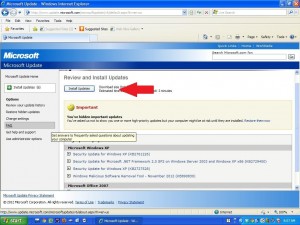
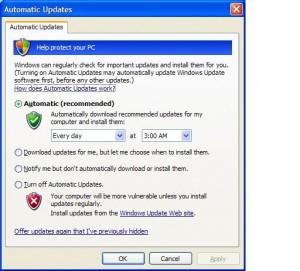
Windows Updates:
This one is extremely important and super easy to do. Probably 75% of the computers I sit down with have pending security updates for Windows, Adobe, Java, etc. Hackers are constantly identifying and exploiting security vulnerabilities in a variety of popular applications. In some cases, they are able to exploit these holes and take control of your computer. Make sure that Windows Update is enabled and that you’re applying the critical and important updates on a regular basis. Also, be sure to apply updates to other programs that notify you in the system tray. Adobe and Java have been particularly susceptible to security issues over the last few years, so make sure you’re keeping the patches applied.
Use Strong Passwords
This one warrants its own post, so take a look at my discussion on passwords.
Other Stuff:
There are plenty of other precautions you can take to stay safe, such as demoting your user account to Standard instead of Administrator, avoiding suspicious links in emails and Facebook, and periodically backing up your data. However, all this talk about security is making me hungry. Think I’ll grab a double latte and a scone. Can someone watch my laptop while I wash up?
Stay safe out there!